Encryption plays an important role in securing digital communication and transactions. A public key is a fundamental component of asymmetric cryptography, a system that enables secure data exchange without requiring both parties to share a secret key. Public keys are widely used in online security, email encryption, and cryptocurrencies.
In blockchain technology, public keys generate wallet addresses for cryptocurrency transactions, allowing users to receive funds securely. Since blockchain transactions are publicly recorded, factors such as security, market demand, and public trust can influence cryptocurrency prices and larger financial trends over time. Public-key cryptography remains an essential component of modern digital security.
How Do Public Keys Work?
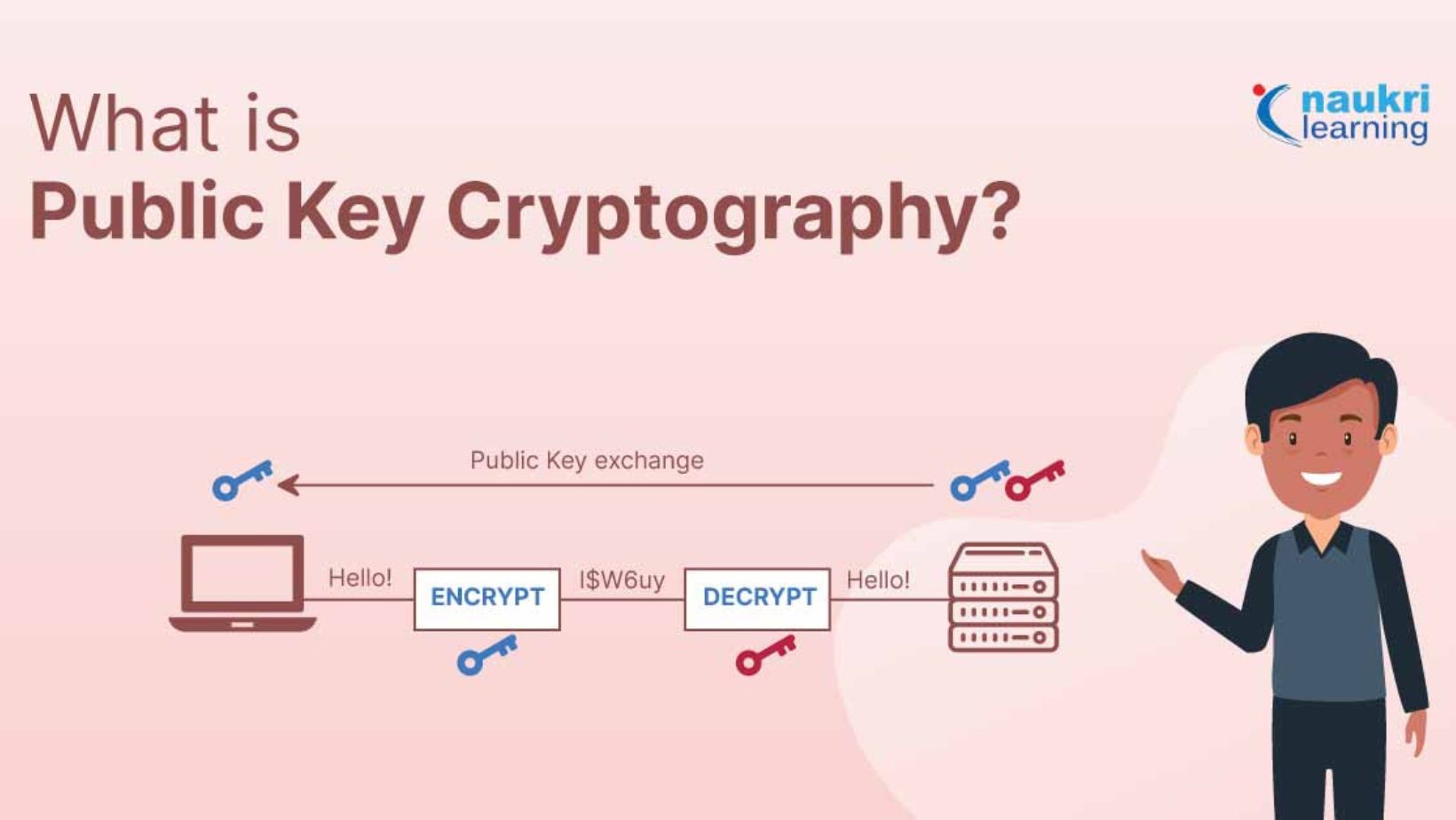
Public-key cryptography relies on an asymmetric encryption system where two keys, a public key and a private key, work together to secure data. The public key is freely shared and used to encrypt messages or verify digital signatures, while the private key remains confidential and is used to decrypt messages or create digital signatures.
For example, when sending an encrypted email, the sender uses the recipient’s public key to encrypt the message. Only the recipient, who holds the corresponding private key, can decrypt and read it. Similarly, in digital signatures, the sender signs a document with a private key, and anyone can verify its authenticity using the public key. This system ensures that even if a public key is widely available, encrypted data remains secure, as only the matching private key can decrypt it.
Public Keys in Cryptocurrencies
Public keys play a critical role in cryptocurrency transactions by enabling secure and transparent transfers of digital assets. When creating a cryptocurrency wallet, a public key is generated alongside a private key. The public key is then used to create a wallet address, which can be shared to receive funds. However, only the corresponding private key allows access to the funds.
Public-key cryptography ensures that transactions remain secure. When sending funds, the sender uses the recipient’s public key to direct the transaction, while the private key verifies ownership and authorizes the transfer. This system prevents unauthorized access and ensures that only the rightful owner can control their assets.
What Are the Differences Between Public and Private Keys?
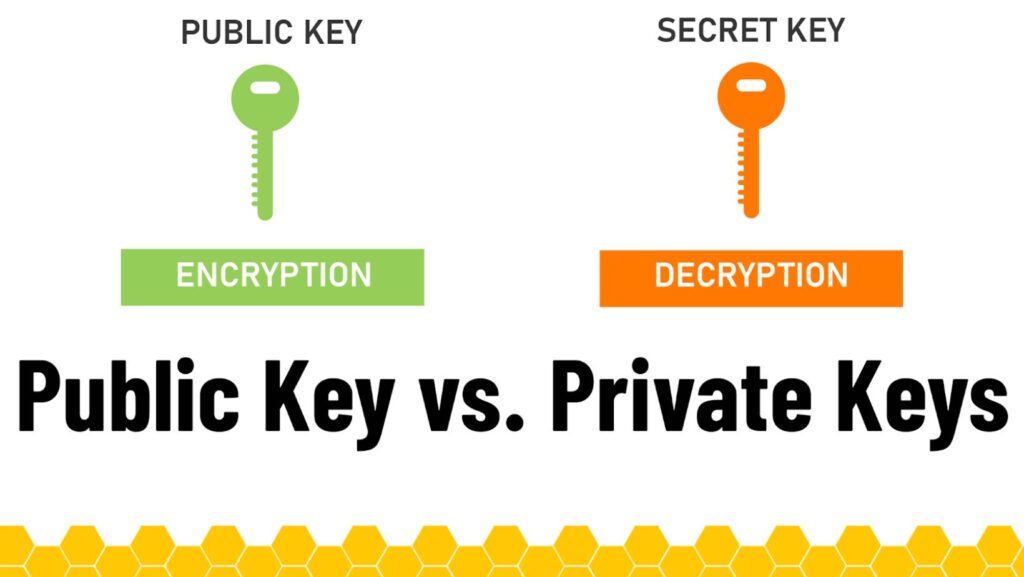
Public and private keys serve distinct but complementary roles in cryptographic security. A public key is designed for encryption and verification. It can be freely shared, allowing others to send encrypted messages or verify digital signatures. In contrast, a private key is used for decryption and signing transactions, and it must remain confidential to prevent unauthorized access.
For example, in cryptocurrency transactions, a public key generates a wallet address, enabling others to send funds. However, only the corresponding private key can authorize withdrawals or transfers. If a private key is compromised, the associated funds or encrypted data can be stolen, making it crucial to store private keys securely.
Public keys are visible on blockchains and other digital platforms, enhancing transparency without exposing sensitive data. Private keys, on the other hand, act as the ultimate safeguard. Losing a private key can permanently prevent access to funds or data.
What Are Common Uses of Public Keys?
Public keys are widely used to ensure security, authentication, and data integrity. One of the most common uses is digital signatures, where a private key signs a document or transaction, and a public key verifies its authenticity. This process ensures that data has not been altered and confirms the sender’s identity.
In secure email communication, public-key encryption (such as PGP) protects sensitive messages. Only the intended recipient, with the matching private key, can decrypt the content.
Public keys also play a crucial role in SSL/TLS encryption, securing websites by encrypting data between users and servers. This encryption protects sensitive information, such as login credentials and payment details, from cyber threats.
In blockchain technology, public keys generate wallet addresses for cryptocurrency transactions, allowing users to receive funds securely. They also facilitate smart contracts, enabling self-executing agreements with transparent verification processes. Public-key cryptography remains an essential component of modern digital security.
What Potential Risks of Public Keys?
While public-key cryptography is highly secure, there are some risks. Man-in-the-middle attacks occur when an attacker intercepts or replaces a public key, tricking users into encrypting data for the wrong recipient. Using certificate authorities (CAs) or blockchain-based identity verification can prevent such attacks.
Key exposure is also a risk if private keys are stored improperly. To protect private keys, users should employ hardware security modules (HSMs), cold storage, or encrypted backups.
Another concern is quantum computing, which could break current encryption algorithms. Developing post-quantum cryptography will be necessary to maintain security in the future.
Public Keys: The Foundation of Digital Security
Public keys are essential for encryption, authentication, and secure transactions. They enable safe communication, protect digital assets, and power blockchain technology. While public keys enhance security, safeguarding private keys is critical. As technology evolves, public-key cryptography will remain a cornerstone of online security.